This article describes Google's Inactive Account Manager, a new tool that gives you control over what happens to your Google account if you don't log on to it for a period of time.
Ages ago, I read a thought-provoking article on ProBlogger about making a "blogging will". His main aim was to ensure that his family could access his business assets (ie his blogs etc) if something untoward happened to him.
Now, Google's Data Liberation Front have annnounced a new tool called the Inactive Account Manager, which lets Google account owners say what should happen if they ever stop using their account.
This tool lets you decide
At the moment, it covers these Google tools - which are attached to your Google account:
AdSense is a notable exception: I don't know what happens to your outstanding balance and income if your AdSense account becomes inactive. But I suspect that it might be managed in the same way as a bank account or book royalties - and because each country will have different laws about managing estates and the like, it's not possible to let you "opt-out" in the same way as it is for regular data.
In this case, if your blog and other Google content (eg YouTube videos) is personal, you may or may not want family or friends to access it - and you may or may not want it to be deleted.
But if your blog belongs to an organisation or a business, it's quite a different scenario: you will almost certainly want someone else to have access.
And if it contains material about a hobby or public interest topic, you may well want to have it transferred to some kind of "data steward" - or you may want your estate to manage it as an asset, if it is profitable.
Personally, I don't think that losing interest or losing access are likely to happen. So I've set up my IAM information to cover the first case, ie death or incapacity, and used it to send messages to carefully selected friends and relatives. I could do more, eg include details about selling a couple of blogs that would be "assets" in the right hands, and send messages to the firm who would be looking after my affairs. But it's a start - and as with so many "death and taxes" type of issues making a start is half the battle.
Once you have thought about what sort of situations you want to deal with, then setting up your inactive-account information is pretty easy.
To start with, go to the Account Management option your Google account settings page. Once you're there, there is an easy set-up wizard, which covers the following points.
They ask for:
For each trusted contact, you need to give some message-text and also say which specific Google products they should get access too.
You can also set up an auto-reply to messages to your Gmail account, which is sent in response to all incoming messages after your account becomes inactive - or at most once every 4 days if one account sends you lots of messages.
And there are still lots of things that we don't know about how IAM will work in practise.
So while I think that IAM is a great idea, I'm also a little nervous about what problems it could cause if people choose to delete things without thinking through all the consequences.
And if you are going to set it up for your own personal blogs, then maybe now is a good time to transfer ownership of blogs that you made for clubs / societies / organisations / businesses to generic accounts being managed for them.
Team blogs: letting other people write to your blog
Transferring blog ownership
Understanding how Blogger and Picasa-web-albums work together
Setting up AdSense for your blog
Ages ago, I read a thought-provoking article on ProBlogger about making a "blogging will". His main aim was to ensure that his family could access his business assets (ie his blogs etc) if something untoward happened to him.
Now, Google's Data Liberation Front have annnounced a new tool called the Inactive Account Manager, which lets Google account owners say what should happen if they ever stop using their account.
This tool lets you decide
- If and when your account should be treated as inactive
- What happens with your data if it becomes inactive, and
- Who else is notified, and what is said to them.
At the moment, it covers these Google tools - which are attached to your Google account:
- +1s
- Blogger
- Contacts and Circles
- Drive (which I guess means Docs too)
- Gmail
- Google+ Profiles, Pages and Streams
- Picasa Web Albums
- Google Voice
- YouTube.
AdSense is a notable exception: I don't know what happens to your outstanding balance and income if your AdSense account becomes inactive. But I suspect that it might be managed in the same way as a bank account or book royalties - and because each country will have different laws about managing estates and the like, it's not possible to let you "opt-out" in the same way as it is for regular data.
What situations is this for
There are a few scenarios that the IAM ("Inactive Account Manager" is such a mouthful) might be useful for.Death / Serious illness or injury
The most obvious thing that you could use the IAM to provide for is if you unexpectedly die, or become so sick/injured that you cannot log in any more.In this case, if your blog and other Google content (eg YouTube videos) is personal, you may or may not want family or friends to access it - and you may or may not want it to be deleted.
But if your blog belongs to an organisation or a business, it's quite a different scenario: you will almost certainly want someone else to have access.
And if it contains material about a hobby or public interest topic, you may well want to have it transferred to some kind of "data steward" - or you may want your estate to manage it as an asset, if it is profitable.
Losing access to your account
Some people lose access to their Google account because they:- Set them up with an external email address
- Lose access to that email address
- Forget the Google account password
- Cannot remember enough details to regain access via the forgotten-password wizard.
Losing interest in your account
People's lives and priorities change over time. The blog that was all-important ten years ago may now be a distant memory. In this case, if IAM is set up, people will at least get a chance to think about whether they want to maintain what was there, or notThe best approach?
There is no "one right way" to use the IAM to look after your blog when you stop updating it. It's a very private decision, and depends on what risks you think you want to cover off, and how you are using your Google account.Personally, I don't think that losing interest or losing access are likely to happen. So I've set up my IAM information to cover the first case, ie death or incapacity, and used it to send messages to carefully selected friends and relatives. I could do more, eg include details about selling a couple of blogs that would be "assets" in the right hands, and send messages to the firm who would be looking after my affairs. But it's a start - and as with so many "death and taxes" type of issues making a start is half the battle.
How to set up your inactive account information
Once you have thought about what sort of situations you want to deal with, then setting up your inactive-account information is pretty easy.
To start with, go to the Account Management option your Google account settings page. Once you're there, there is an easy set-up wizard, which covers the following points.
Warning that you're in danger of becoming inactive
Google doesn't want your account to suddenly become inactive. So they collect details are used to warn you by sending a text message to your cellphone and email to an alternative address, saying that your account is close to becoming inactive. The current definition of "close" is one-month. Basically, this is your chance to stop the account becoming inactive by logging in.They ask for:
- A mobile phone number (which needs to be verified - so it must be one that you can access now)
- An alternative email address (which isn't verified - yet!)
Setting the timeout period
You need to choose how much time needs to go by without you logging in before your account is considered to be inactive. The default is three months, and other options are six, nine and 12 months.Who else to tell
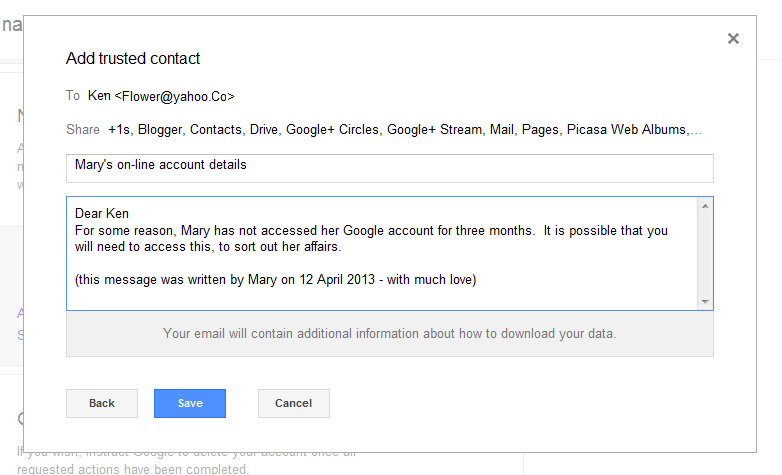
You can nominate one or more trusted contacts - ie email addresses that receive notification, and (if you choose, access to your data), once your account actually becomes inactive.For each trusted contact, you need to give some message-text and also say which specific Google products they should get access too.
You can also set up an auto-reply to messages to your Gmail account, which is sent in response to all incoming messages after your account becomes inactive - or at most once every 4 days if one account sends you lots of messages.
What happens to your account:
Finally, you choose whether to delete your data once your account is inactive - the default value is "no", but you should change it to "yes" if you want to be sure that your blog etc are removed.Confirmation
After you have saved your settings, you will get an email confirming that you entered. (In my case, this message took several days to arrive - possibly because I get up my IAM settings fairly shortly after it had been introduced. Hopefully it's got quicker now.Limitations of the IAM
At the moment, IAM lets you set thresholds, notifications and actions for a whole Google account - there is no way to say that some blogs should be kept, and some deleted.And there are still lots of things that we don't know about how IAM will work in practise.
- Do you get only one reminder - or one every time you reach the inactive-account threshold again (ie every 3, 6, 9 or 12 months)?
- What happens if you're one administrator of a team blog, and your account becomes inactive with instructions to delete it - but there are other member or administrators who are still actively contributing? (I would hope that the presence of these people means that your "delete" instruction is ignores, at least for the blog. But I suspect that this won't be an easy scenario to provide for - and it's possible that Google haven't worked through all the options here.
Ditto other shared resources (YouTube Channels, Shared folder/documents in Drive, etc)? The dimensions will be different in each product, but the underlying problem is the same.
So while I think that IAM is a great idea, I'm also a little nervous about what problems it could cause if people choose to delete things without thinking through all the consequences.
And if you are going to set it up for your own personal blogs, then maybe now is a good time to transfer ownership of blogs that you made for clubs / societies / organisations / businesses to generic accounts being managed for them.
Related Posts
Understanding Google accountsTeam blogs: letting other people write to your blog
Transferring blog ownership
Understanding how Blogger and Picasa-web-albums work together
Setting up AdSense for your blog